990 million compromised and exposed data records over a period of one year across the globe sound alarming, doesn’t it? That’s the number that IBM X-Force research gives us when it examines security breaches in the firms, and finds misconfigured cloud workloads as the primary reason for cybersecurity threats. Additionally, there is a 20% year-over-year increase in the number of publicly disclosed incidents attributed to cloud misconfiguration. This blog aims at helping Chief Information Security Officers (CISOs) and Chief Technology Officers (CTOs) of the fintech companies in solving a critical challenge of such misconfigurations and how they can protect their infrastructures. We also discuss how fintech companies like Cred solved the challenge of cloud misconfiguration.
What is Cloud Misconfiguration?
Cloud misconfiguration is a major compliance risk that can unknowingly expose a company’s unencrypted data to the public without authentication set up. When a company doesn’t configure the cloud-based platform or system in a correct way and leads the door open to attackers and hackers, it is called cloud misconfiguration. It can take many forms, such as-
- Improper network functionality
- Storing encryption keys and passwords in open repositories
- Creating public accessibility to storage buckets
- Unrestricted access to exposed data stored on the cloud
Examples of data and security breaches are countless, but one that’s worth taking notice of is the FedEx security breach in 2018. The company unknowingly exposed thousands of scanned documents including drivers’ licenses, passports, and delivery mail forms due to the company’s inability to secure its AWS cloud storage server.
Cloud Misconfiguration: A Critical Security Threat for FinTech
Cloud-native platforms have become bait for fintech companies to build resilient and agile application architectures, but the truth is that compromised cloud security is the biggest threat that would stop established players in financial services and fintech companies from using cloud capabilities to their full potential. And, 62% of the IT and cybersecurity professionals surveyed by Crowd Research Partners identified cloud misconfiguration as the most critical threat to data and security.
Classic cloud misconfiguration reasons include-
- Unrestricted Outbound Access
- Unrestricted Access To Non-HTTP/HTTPS Ports
- Unrestricted Inbound Access On Uncommon Ports
- Unrestricted ICMP (Internet Control Message Protocol) Access
While the cloud assets are on a rise, the attackers are increasingly using cloud-based messaging and storage services to blend into legitimate traffic. And some groups are experimenting with new techniques in encryption and code obfuscation to go unnoticed. The more time attackers have inside the compromised security environment of an organization, the higher the cost of a breach- $5 trillion to be precise, industry research says, and a vast majority of these breaches are a result of cloud misconfiguration. Also, longer periods of undetected attacks give hackers access to more accounts, devices, and data pieces.
This has raised many alarms across Information Security teams of the fintech companies, while also posing some serious questions- how effectively are they protecting their customers’ data and securing their own digital assets? What are they doing to overcome this challenge? One of the critical questions is also about the Mean Time to Detect (MTTD) for such attacks.
How to Eliminate Cloud Misconfiguration Challenge?
When it comes to protecting digital identities, and securing valuable data some steps can help businesses in avoiding data breaches. Valuebound suggests the following methods on how FinTech companies can eliminate cloud misconfiguration challenges (Fig. 1)
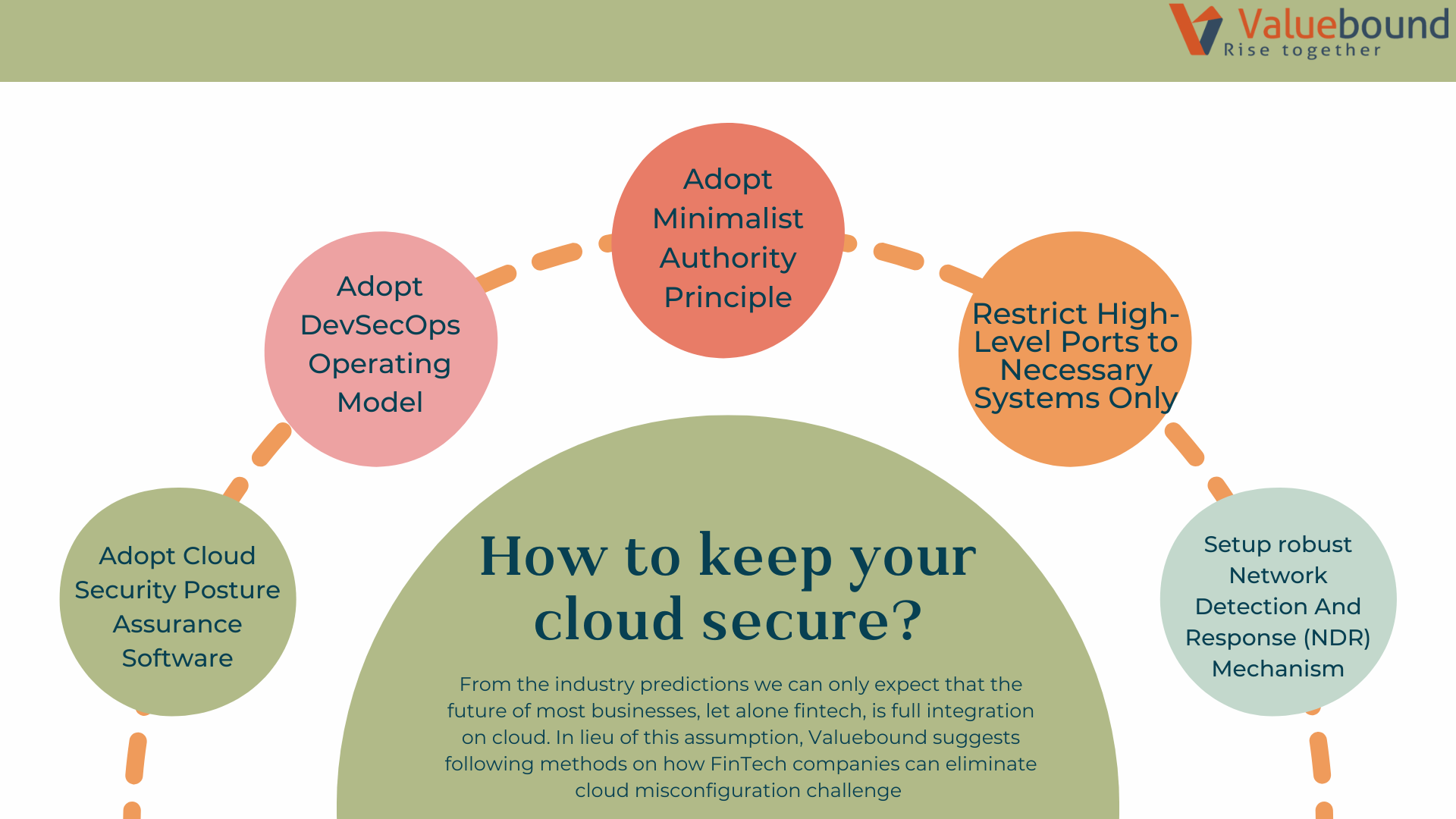
Adopt Cloud Security Posture Assurance Software
Cloud helps with standardization and automation. Hence, the conventional security assessment methods with required manual auditing can be done away with. Cloud security posture assurance software is the answer because by calling cloud platform APIs, it retrieves real-time and actual configurations of cloud resources that have been consumed. Thereafter, the software compares it with the set standard, which allows organizations to understand baseline deviations through reports and dashboards. Such software and products can typically facilitate compliance reporting for various regulations, laws, and frameworks including PCI, HIPAA, CIS, and NIST.
Adopt DevSecOps Operating Model
Many fintech executives are already recognizing a trending security shift towards DevSecOps operating model. If your organization is adopting security assessment methods, it is also essential to understand that integration of security in the process of continuous governance is a must. At the focal point of the DevSecOps operating model is setting up a security baseline which acts as a yardstick for monitoring and tracking actual status or issues through resolution. DevSecOps also implement continuous compliance assurance to check risk exposure and actual status of compliance.
Adopt Minimalist Authority Principle
Outbound traffic must use the minimalist authority principle to combat the challenge of unrestricted outbound access. A common practice among the majority of AWS users is to configure inbound ports in the security groups while forgoing outbound ports. Imposing limitations on outbound traffic can direct traffic only to servers and applications which need to communicate. This helps in bringing down the risk of data exfiltration, internal network scans, and lateral movement. The servers may also require RDP (Remote Desktop Protocol) or SSH (Secure Socket Shell) inbound ports in managing them.
Restrict High-Level Ports to Necessary Systems Only
Many services use TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) internet protocol suites and ports to obfuscate what’s running in their cloud environment, but this is not enough. It will not protect your organization from random internet scans or a smart hacker. Some of the services can open uncommon ports too, which often go off the radar. In such a case, you must ask if your web server has a statistics page or PHPMyAdmin functioning on port 8443, or Apache Tomcat services leak on port 8080. High-level ports are ideal to be restricted only to necessary systems.
Block ICMP
ICMP (Internet Control Message Protocol) is among the most important protocol, and leaving it unattended on the internet can expose your fintech company to vulnerable attacks. ICMP’s most common practice is using ICMP Echo for verifying is the servers are responsive and online. ICMP Echo, therefore, acts as a top-notch diagnostic tool for security professionals. But here’s a catch. It is also an excellent tool for hackers who can use Nmap or Fping to ensure that your server is indeed online. So what’s your best bet? Block ICMP!
Setup Robust Network Detection And Response (NDR) Mechanism
Until the most recent times, it was very difficult to parse and capture network traffic in the cloud, which was one of the critical reasons why cloud security lagged behind conventional security. But with the network detection and response (NDR) mechanism monitoring network communication in real-time became possible. It is hence seen as the easiest and quickest way to stay ahead of hackers in a dynamic and complex ecosystem. NDR enables rapid threat detection and deep visibility on-premises, in real-time. The gap is also closing in with the advent of Azure and AWS traffic mirroring solutions.
How Fintech Firms Solve Cloud Misconfiguration Challenge?
“One of the crucial Key Performance Questions (KPQ) for any incident response process is to continuously improve and reduce Mean Time to Detect (MTTD) from days to seconds,” says CRED. To solve the critical challenge of cloud misconfiguration, CRED uses the tool DIAL (Did I Alert a Lambda?).
DIAL is an automated tool that monitors, detects, and alerts cloud misconfigurations across all its AWS accounts. DIAL overview (Fig. 2) shows how its inbuilt detection mechanism works to prevent common misconfiguration mistakes that can jeopardize AWS infrastructure.
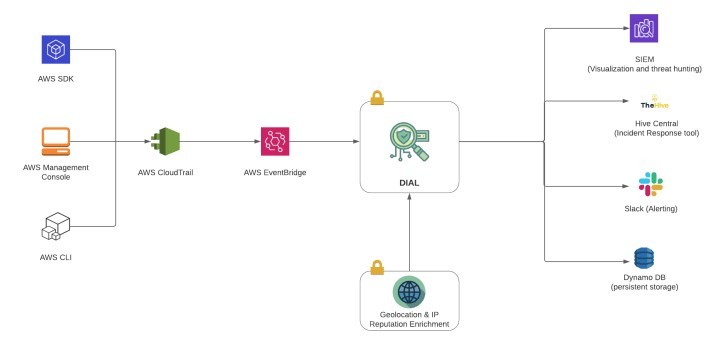
Composed of a bundle of AWS services like EventBridge, API Gateway, and LAMBDA, DIAL is deployed in Master-Worker architecture and is ideal for use in AWS organization. With DIAL’s deployment, CRED’s MTTD is anywhere between 4 seconds to 10 seconds only. That is how CRED uses DIAL’s capabilities to reduce average detection time, and scale at large.
Select a vendor with proven product capabilities
Bringing managers at infrastructure management, security operations centers, information security, and DevOps to have a common understanding of cloud misconfiguration can help an organization implement best practices for cybersecurity for the cloud.
A vendor with proven product capabilities and best practices in implementing such cloud security assurance processes, along with introducing newer opportunities can transform your product into an integrated digital asset with high-level, unbreachable security. If you are looking to partner with one such vendor, drop us a hello and we would be happy to engineer solutions for your challenges.





