Cloud computing is such a popular topic, because it was built to reduce cost and save resources. With the growing demand of online presence and digitization of news, it is the need of the hour for Media and publishing enterprises and all leading Publishing houses to take it into serious consideration to move a chunk of the work from their data centers and networking centers over to Cloud to reap the benefits of less spends and less maintenance, however the Cloud Computing Technology comes with certain liabilities as threats and vulnerabilities, in this post we go through what exactly to expect from Cloud in terms of security.
Vulnerability: Vulnerability is a prominent factor of risk. ISO 27005 defines risk as “the potential that a given threat will exploit vulnerabilities of an asset or group of assets and thereby cause harm to the organization,” It is seen as an opportunity for attackers to exploit for personal gain, measuring it in terms of both the likelihood of an event and its consequence.
Threat: Threat is an entity that attacks system takes advantage of its vulnerabilities and uses the exploit to his own advantage.We often tend to confuse and blur the line between security issues in Cloud and security issues in general.
When is a Vulnerability Cloud Specific?
- If it is intrinsic core cloud computing technology
- If it has relation to one of NIST’s cloud characteristics
- When technology is upgraded in Cloud and that makes security mechanisms tough to be implemented
- Already present in Cloud
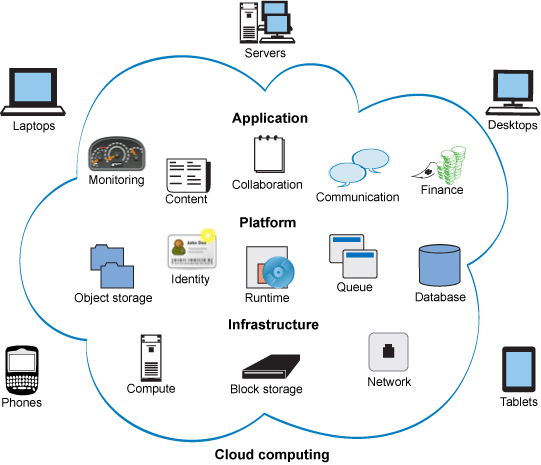
Cloud computing vulnerabilities
When deciding to migrate to the cloud, we have to consider the following cloud vulnerabilities:
Session Riding
Virtual Machine Escape
Reliability and Availability of Service
Insecure Cryptography
Data Protection and Portability
CSP Lock-in
Internet Dependency
Cloud computing threats
Before deciding to migrate to the cloud, we have to look at the cloud security vulnerabilities and Cloud Computing threats to determine whether the cloud service is worth the risk due to the many advantages it provides. The following are the top security threats in a cloud environment
Ease of Use
Secure Data Transmission
Insecure APIs
Malicious Insiders
Shared Technology Issues
Data Loss
Data Breach
Account/Service Hijacking
Unknown Risk Profile
Denial of Service
Enterprises are adopting the cloud computing services in every day operations, but it’s often not the case they really understand what sort of thing is coming next. Cloud users should know the good and bad about the attacks and about the links that are weak. There are multiple ways a black hat hacker can do to dig into the system and cause damage. Security awareness is an often overlooked security concern.
Image Credit : http://core0.staticworld.net/